Airwall — Remote Access / Software Defined Perimeter (SDP)
Network boundaries are disappearing. Remote workers and devices need access to resources on-premises and in the cloud. IoT and OT devices need to be both protected and isolated from other systems, yet remotely managed and serviced. Existing tools like firewalls, VLANs and VPNs have failed at providing the flexible, automated network perimeter with granular access to individual devices that organizations now typically need.
A Software Defined Perimeter uses a zero trust approach to create a more dynamic private network for remote access to any set of devices across any network. Policies are easily managed and aligned with device or user identities. Compared to existing remote access of VPN solutions, Tempered Airwall provides an end-to-end encrypted overlay network to ensure not only secure remote access without chance for broader network access, but eliminated man-in-the-middle attacks or spoofed credentials.
Airwall is the run-anywhere platform for secure networking.

WHITEPAPER
A Software Defined Perimeter uses a zero trust approach to create a more dynamic private network for remote access to any set of devices across any network. Policies are easily managed and aligned with device or user identities. Compared to existing remote access of VPN solutions, Tempered Airwall provides an end-to-end encrypted overlay network to ensure not only secure remote access without chance for broader network access, but eliminated man-in-the-middle attacks or spoofed credentials.
Airwall is the run-anywhere platform for secure networking.
Download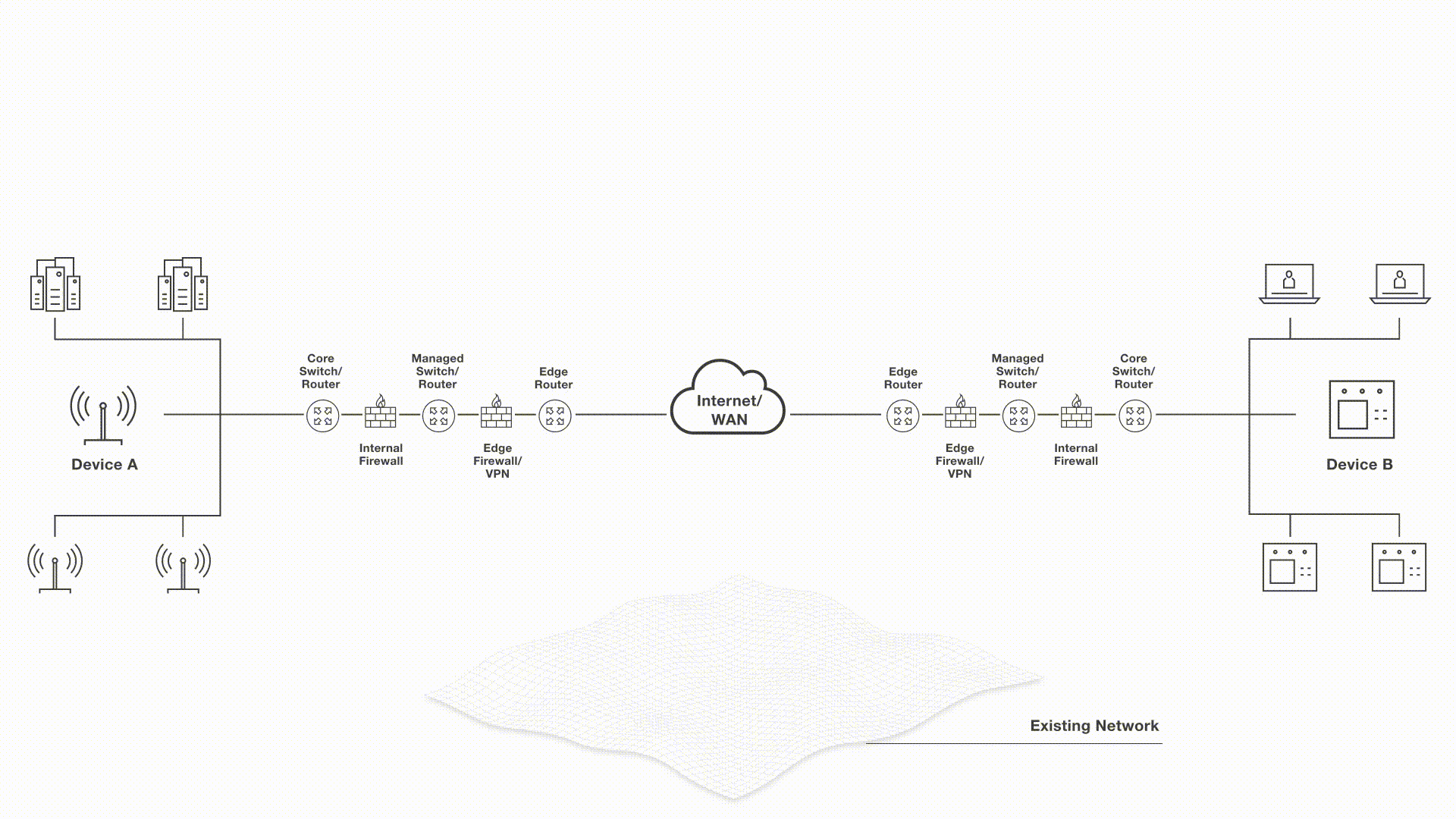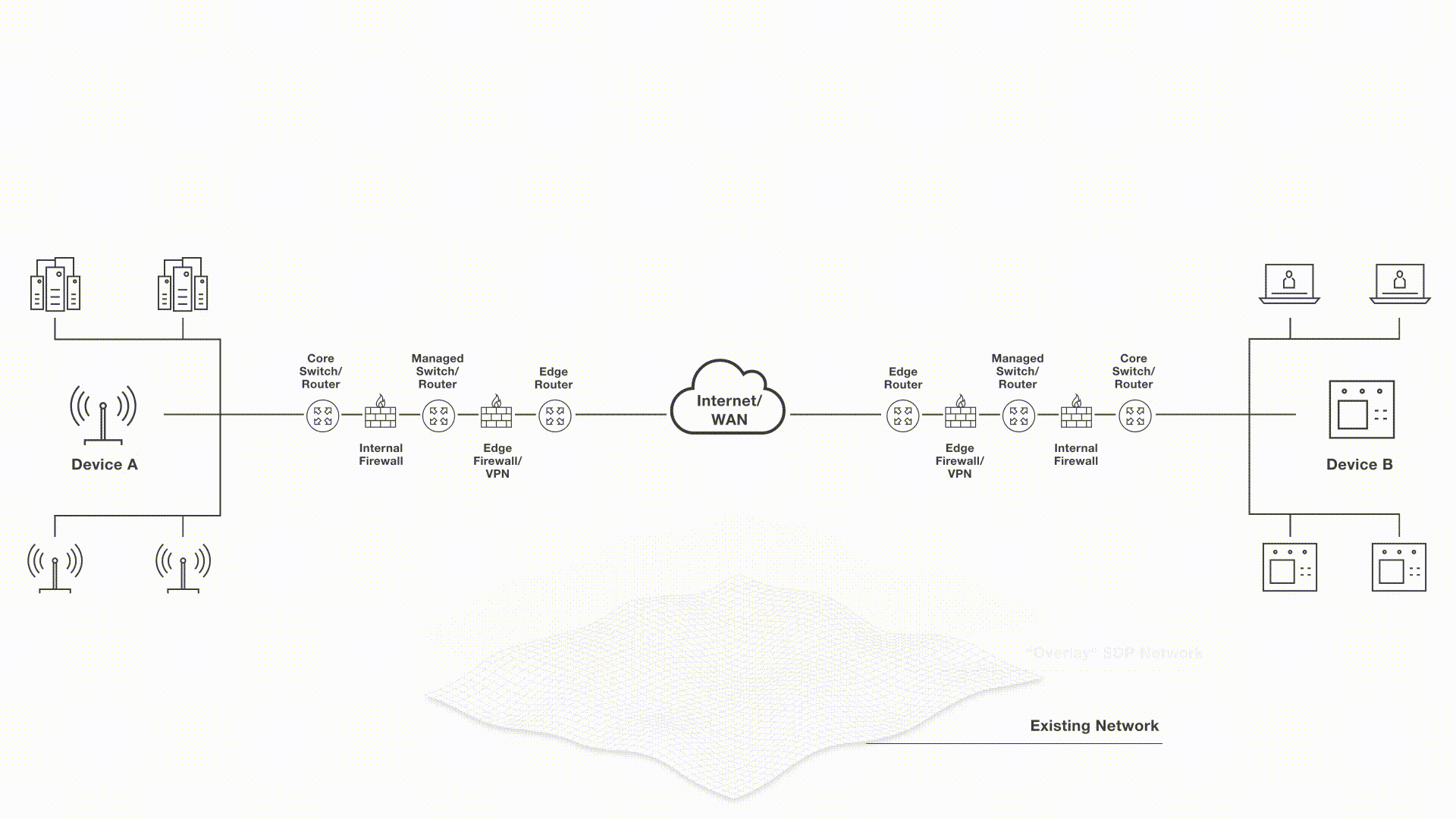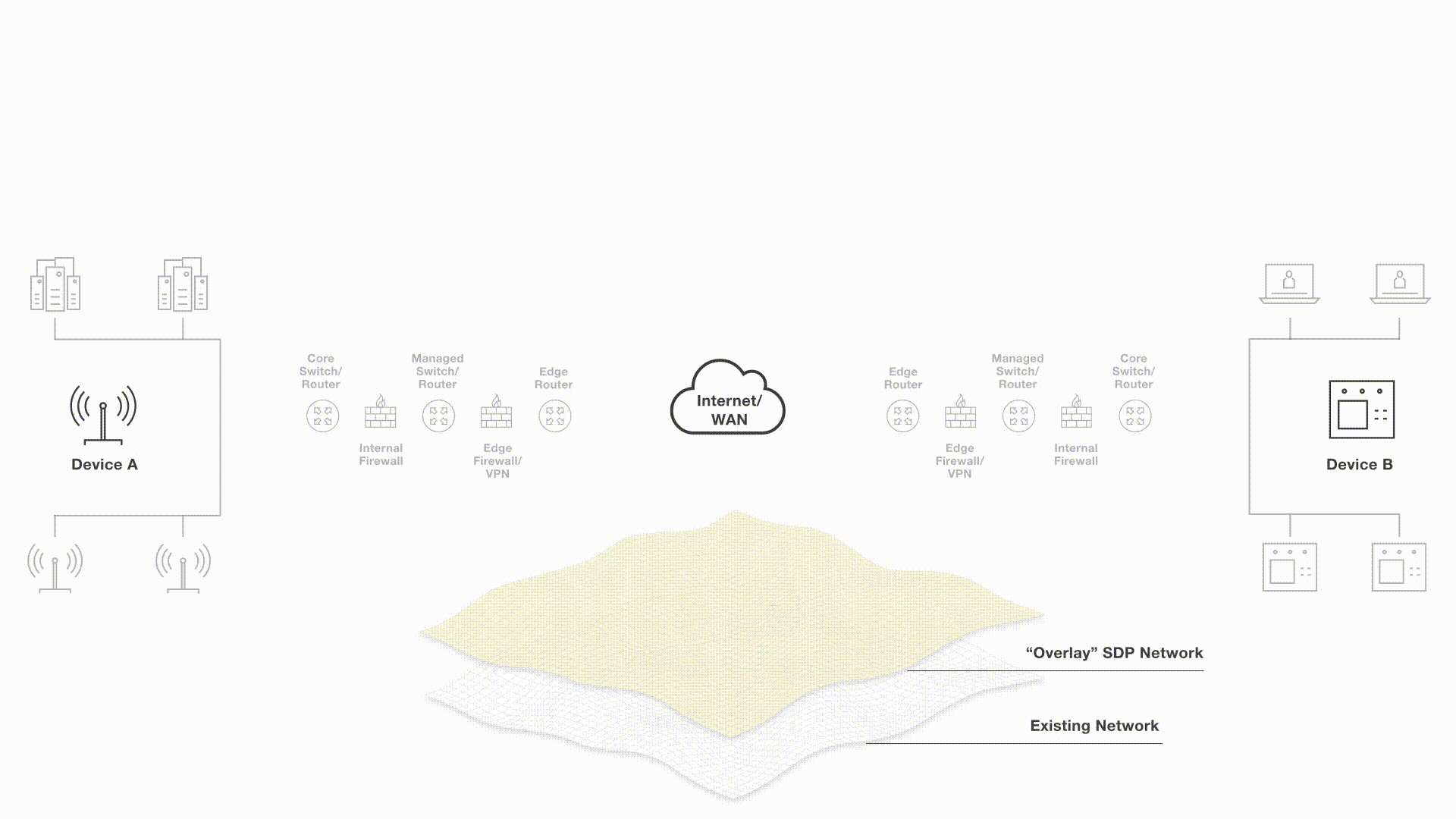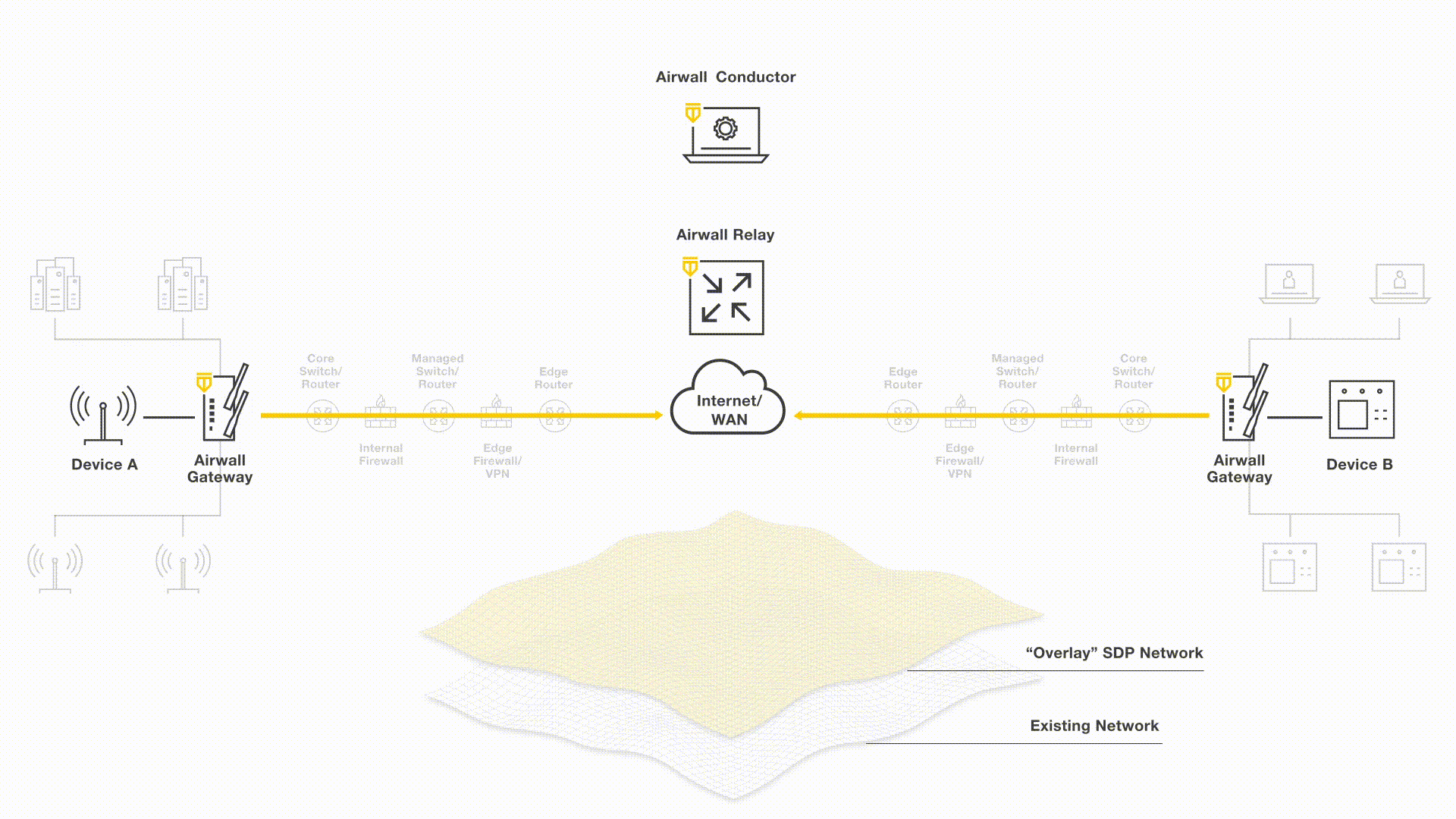
Tempered Networks zero trust remote access solution establishes an encrypted overlay tunnel between any systems over any network. The overlay network removes the ability to orchestrated the complex routing topology and WAN connections with the right security policies. Tempered orchestrates the setup of the encrypted tunnels and the access policies from a centralized controller, the Conductor.
Benefits
Better security:
- Segment & Protect Critical Assets: Restore the virtual air gap
- Encrypted end-to-end
- Reduce Attack Surface: Harden and cloak devices, making them invisible to unauthorized users; virtually shielding 95% of vulnerabilities
- Prevent Lateral Movement: Contain malware and ransomware and stop insider from unauthorized access
Lower Costs:
- By simplifying how secure connections are defined and enforced
- Deploys quickly and easily in 10% of the time of comparable solutions
- Without the need for additional full-time head count
- No fork-lift upgrades, no vendor lock-in to a particular architecture

