Secure by design - fixing the inherent flaw in IP
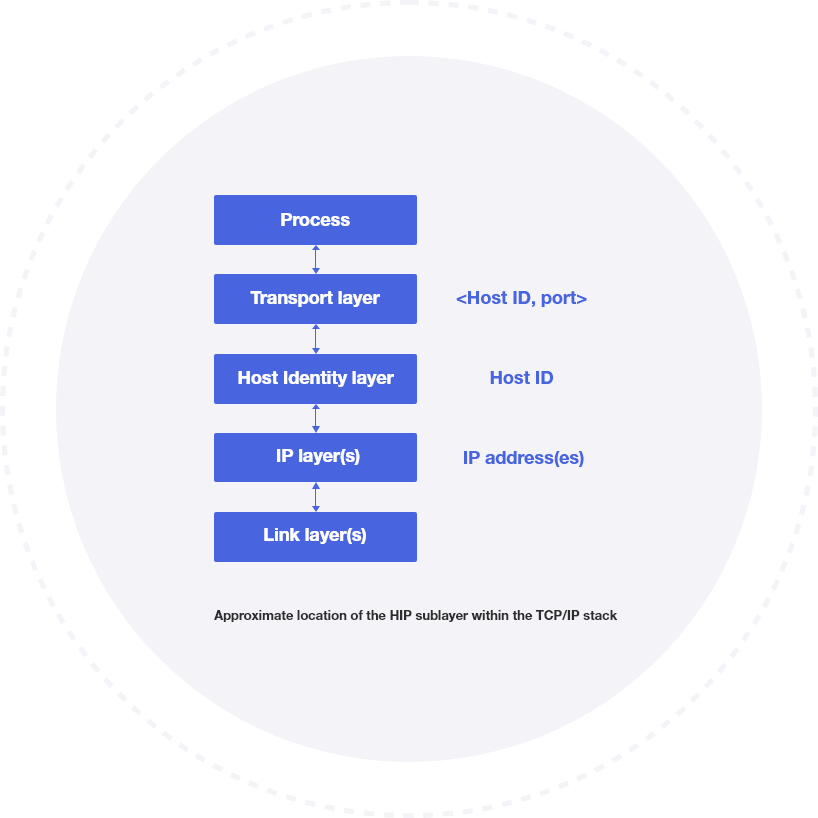
HIP fundamentally provides a secure overlay fabric over existing network infrastructures and introduces a new cryptographic host identifier separate from the usual IP address. The fact that IP addresses include both route information and host IDs has complicated security policy management for decades. The new HIP ID allows for simplified, centralized management of end-point access control policies. The creation of a secure overlay network and the encrypted identifier renders hosts completely invisible to unauthorized users and potential attacks.
Rather than probing an IP device for vulnerabilities, attackers will never know of the existence of the host on the network. To them, the device is completely cloaked. This is the fundamental shift for Tempered Airwall compared to other zero trust and remote access solutions, reducing attack surfaces by upwards of 90% in most deployments.