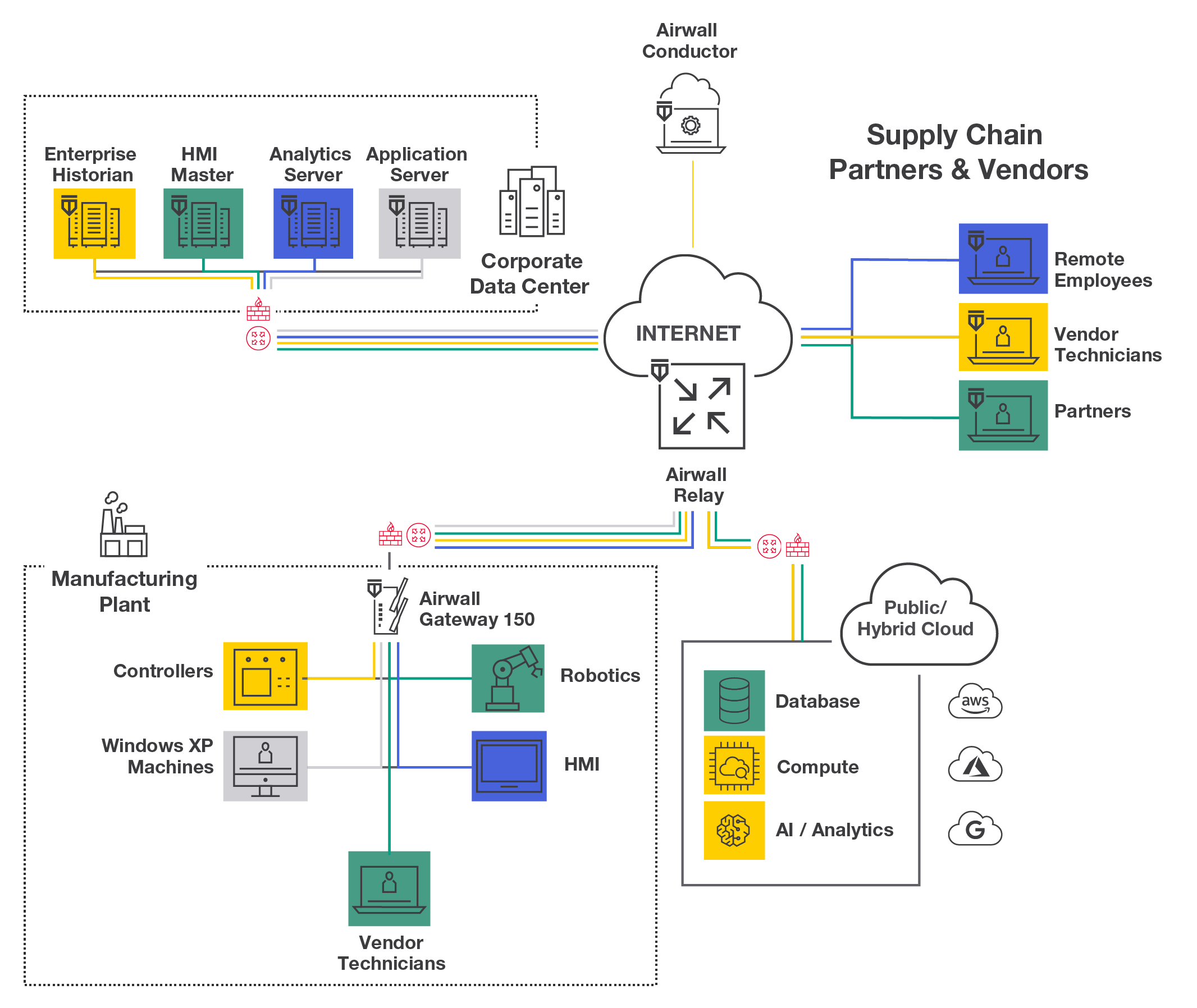
Granular security, approaching whitelisting, where every authorized access from every device can be specified, can reduce the lateral spread of malware if a host becomes infected. This can dramatically improve network security and mitigate threats when all other measures fail.
The benefits of micro-segmentation have already been established by industry experts, government frameworks, and regulatory agencies like PCI DSS and HIPAA. But there can be challenges to deploying micro-segmentation: cost, complexity, and integrating with existing systems. Traditional tools like VLAN’s, firewalls and remote access solutions were not designed for such a granular policy approach.