Critical Manufacturing
Securing modern manufacturing operations takes a new approach, one that takes into consideration:
Service level availability and resiliency as the highest priority.
Scale of connected devices and inter-connected operating partners is only increasing.
Costs and complexity must be kept to a minimum.
By converging traditional operational technology (OT) with existing information technology (IT) systems, and ultimately the Internet, manufacturers are experiencing explosive growth in the number of devices communicating across their networks. Once physically air-gapped silos of critical manufacturing infrastructure, these devices now share the same data communications pathways as front office systems, email, and social media. This creates a more extensive, target-rich attack surface for bad actors that could cause physical damage, facility downtime, breaches of customer data, and intellectual property theft. All of which could lead to loss of business, national security, or even human life.
SOLUTION
Tempered, a pioneer in micro-segmentation solutions for IoT and industrial systems can help manufacturers take full advantage of digital transformation without having to accept growing cybersecurity and privacy risks as a cost of doing business.
The Tempered solution is based on zero trust security where no one is trusted by default from inside or outside the networks, the virtual air gaps, it creates. Verification is required from every Airwall Edge Device to gain access to the protected networks. As such, the Tempered solution works best by establishing trust before connectivity takes place between any devices within your network. All system-level network connections are automatically authenticated and authorized between every endpoint through trusted and verifiable machine identities that cannot be exploited or spoofed. With a single network architecture spanning IT, industrial, virtual, and cloud environments, you can now enforce consistent cybersecurity and privacy across all environments.
Learn more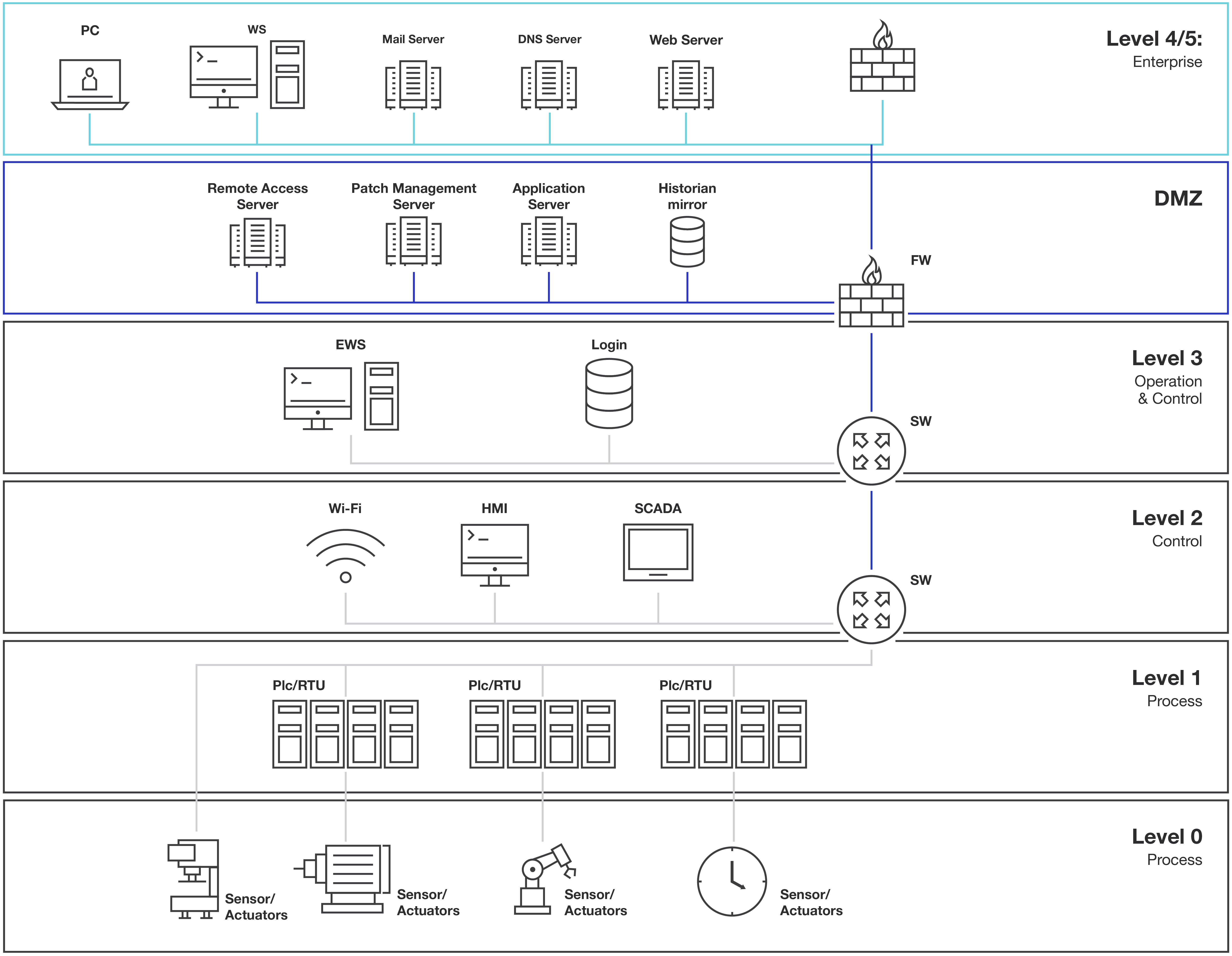
The Purdue Model has been historically used to create security and access zones for various operational levels in manufacturing networks. While used less today because of the increasing connection requirements between OT and IT networks, it's an example of how to begin to segment networks with zero trust and make it more difficult to reach more vulnerable systems.

CASE STUDY
Global manufacturer makes its industrial control systems invisible
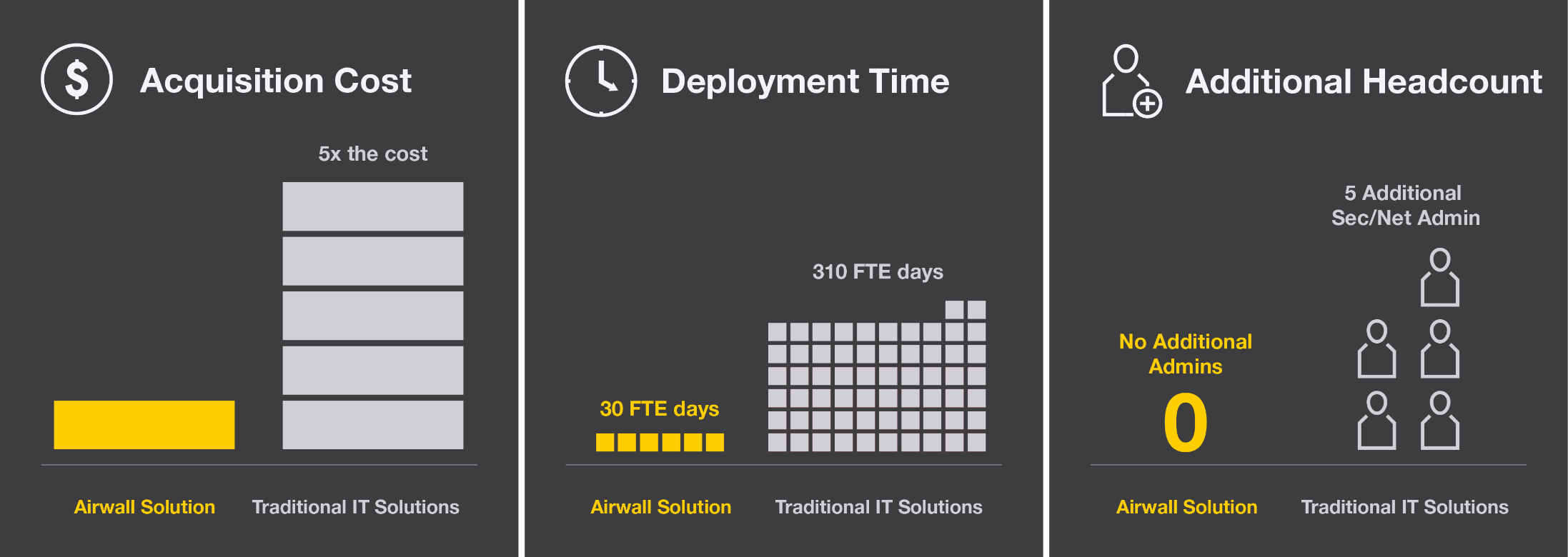
Airwall Solution eliminates network complexity and enables micro-segmentation for a global manufacturer of advanced materials and components.
Download
Why a global manufacturer stopped using interior firewalls to protect critical systems from lateral attacks.
The team covered the first building with over 700 connected systems across 10 different manufacturing lines in half a day without disruption.